List
サブ-ナビゲーション
- Investor Relations
-
Sustainability
- Commitment from Top Management
- Sustainability Management
- Materiality
- Environment
- Social
-
Governance
- Corporate Governance
- Risk Management
- Compliance
- Tax Policy and Initiatives
- 現在位置:Information Security
- Distribution of Economic Value to Stakeholders
- ESG Promotion Activities
- Sustainability Data
- Third-Party Assurance
- Membership in External Organizations
- External Evaluations
- GRI Content Index
- Editorial Policy
- Report Library (Archives)
- Sustainability News
Information Security
Information Security
The Group defines information security as one of the issues in management, and aims to conduct safe business by ensuring information management, including the handling of personal information.
Basic Approach
The Group considers information security as one of its management issues, recognizes the personal information of customers and business partners to be one of the most important information assets, and strives to reduce the risk of information leakage, loss, and destruction.
Management System
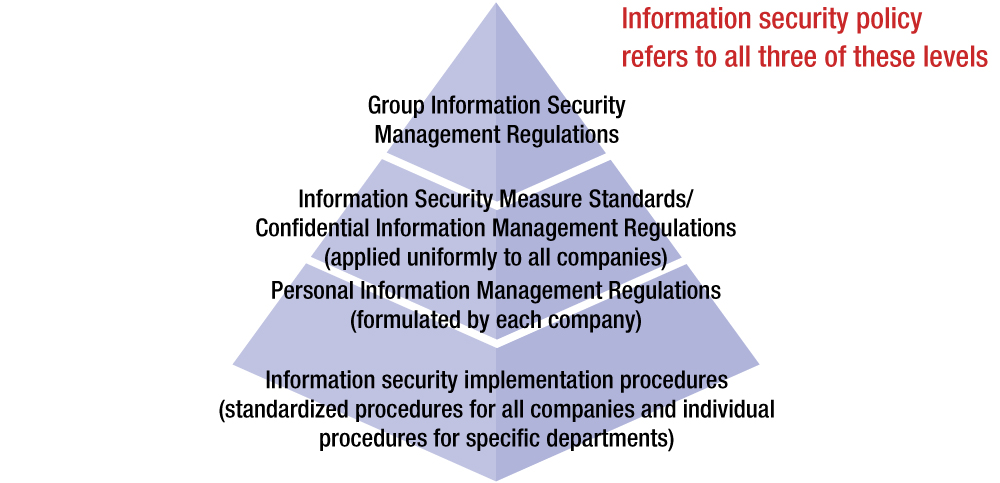
In order to ensure compliance with the Group information security management policy, we have defined Group Information Security Management Regulations, Information Security Measure Standards, Confidential Information Management Regulations, and various implementation procedures that must be complied with.
Group Information Security Management Regulations:
Basic rules regarding the construction and operation of a management system for Group information security, for the goal of protecting the information assets owned or managed by the Group from theft, leakage, modification, or destruction, and minimizing corporate loss.
Information Security Measure Standards:
Standards defining information security countermeasures for electromagnetic information assets that the Group must follow.
Confidential Information Management Regulations:
Basic indicators on management methods for maintaining the confidentiality of information assets in general.
Personal Information Management Policy:
Basic rules regarding the handling of personal information.
Scheme of Information Security Policy and Documentation
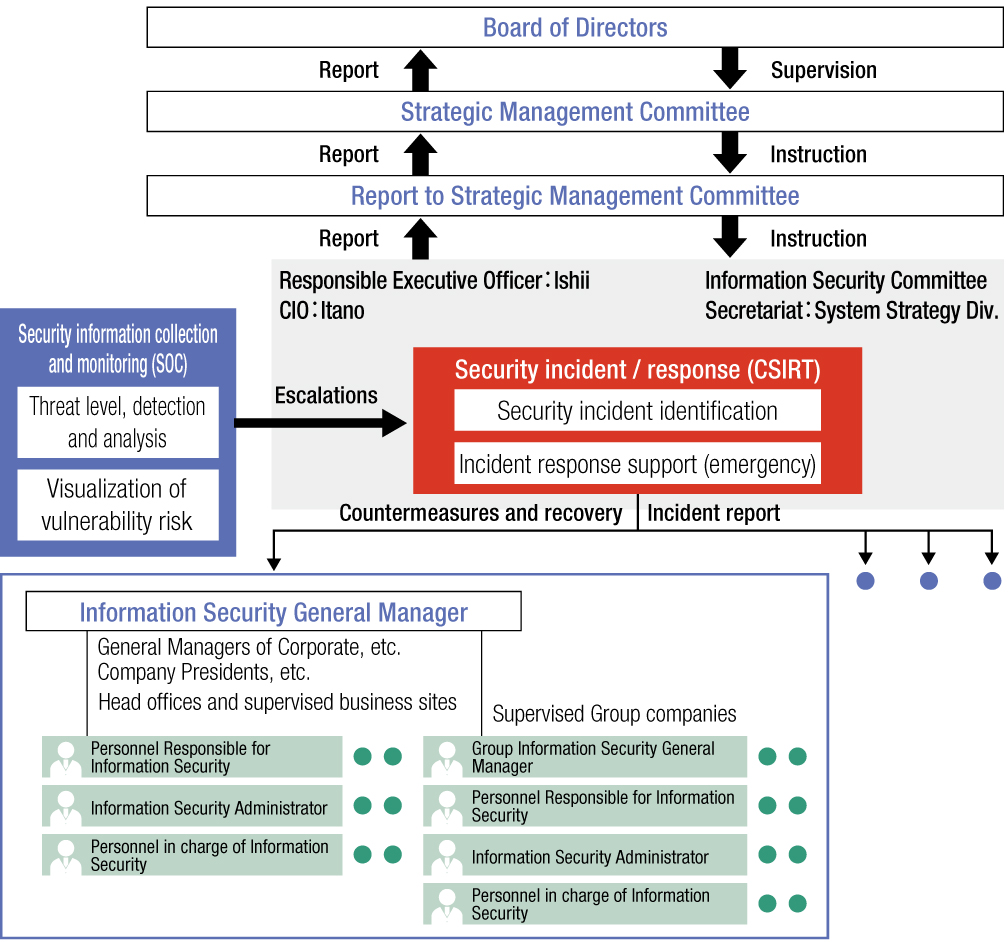
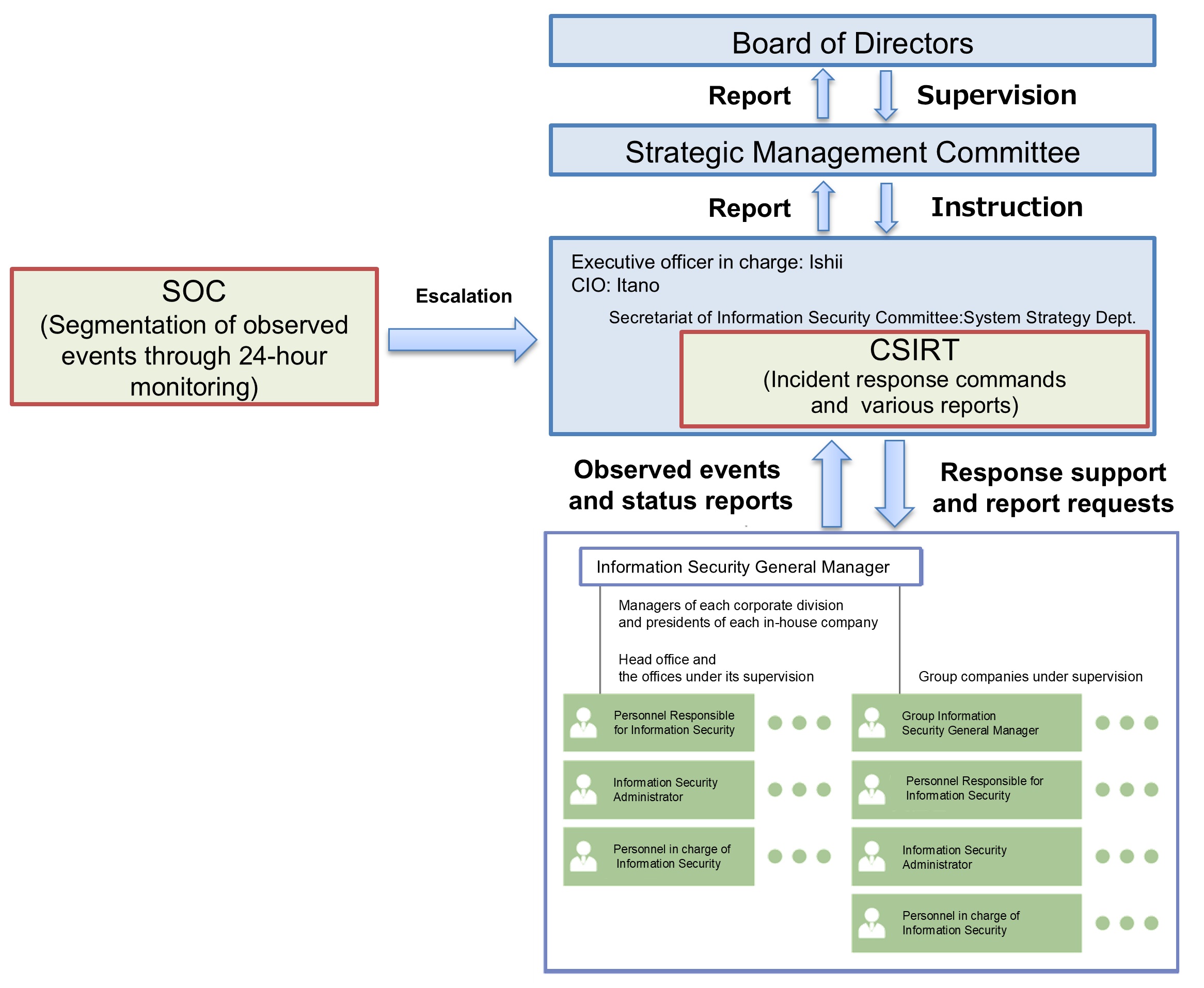
In addition, “Information Security Panels” are set up to establish, adopt, operate, monitor, review, maintain and improve our information security policy, and information security managers are assigned to the Group and Group companies to operate and monitor them.
Information Security Operations and Management Structure
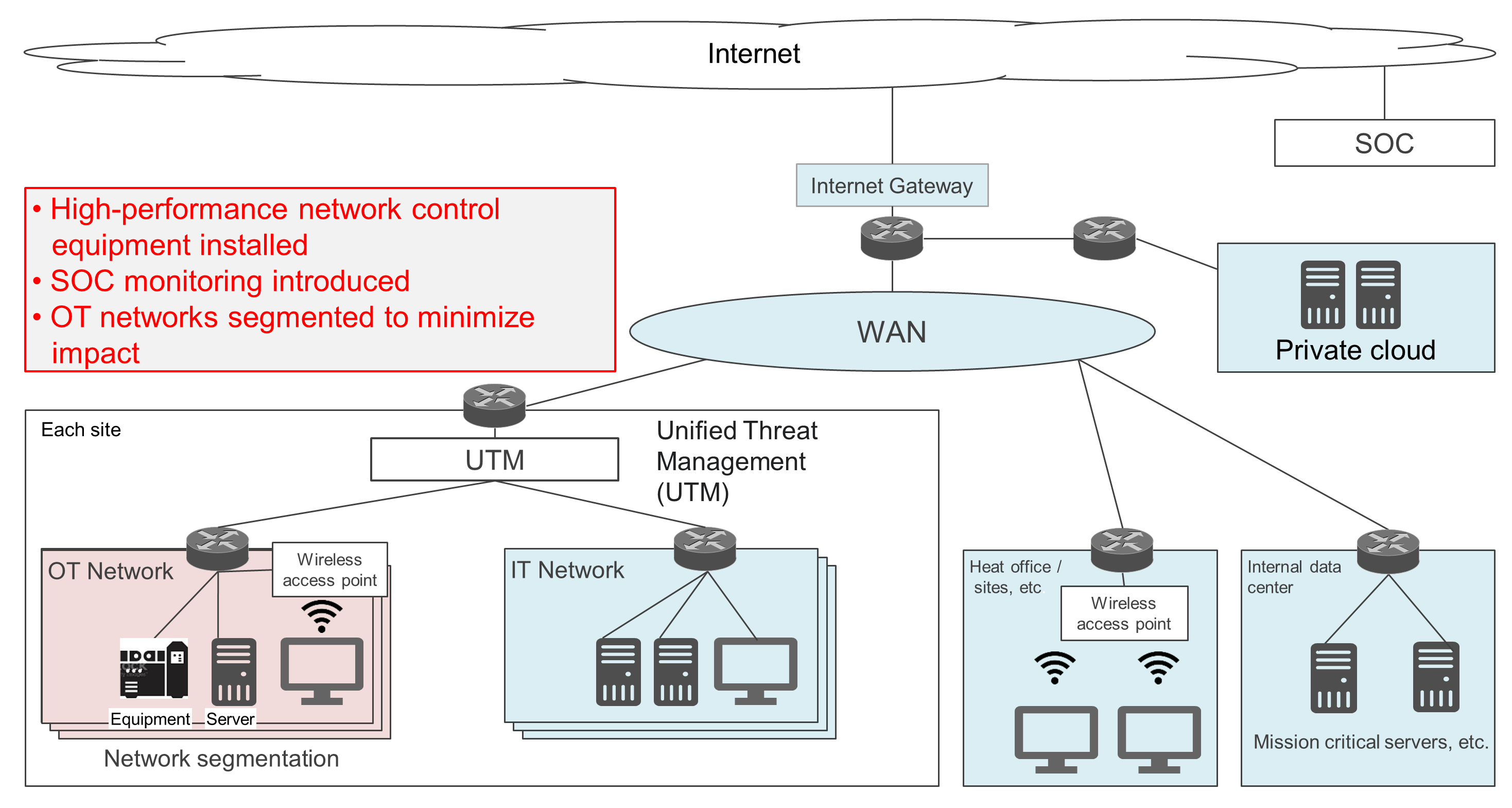
Various Information Security Compliance Initiatives
Our information security activities involve enhancing and expanding our information infrastructure with an eye towards business continuity in the event of a large-scale disaster, strengthening our technical measures for information systems, and introducing and operating management systems. Technical efforts include enhancing our protective measures for preventing damage from attacks that leverage known vulnerabilities, as well as our risk reduction measures, which include enhancing defense in depth and the early detection of damage from new threats such as targeted attacks. In order to counter the rising threat of ransomware, we have introduced a system for forcibly applying updates and patches for vulnerabilities of the Group and all Group companies, including overseas companies.
On the management end, we strive to maintain and improve our level of security by implementing the PDCA cycle of performance evaluations and employee education on a continual basis.
In the fiscal year ended March 2024, we expanded the scope of monitoring to include individual PCs. In the fiscal year ended March 2025, we further extended monitoring to the operational technology (OT) domain and promoted the stable operation of the Security Operations Center (SOC) while expanding the monitored areas. We will continue these initiatives as measures for the fiscal year ending March 2026. In addition, we aim to institutionalize the activities of the Computer Security Incident Response Team (CSIRT) and to enhance and standardize security awareness through information security education and training.
Furthermore, in addition to complying with domestic personal information protection laws and the GDPR, we will comply with the personal information protection laws of relevant countries, while planning the implementation of new security measures in the OT domain in preparation for digitalization and the transition to smart factories, and strengthening supply chain risk management. We have also established guidelines for the use of AI, including external AI services, and intend to make an overview of these guidelines publicly available in due course. At the same time, for cases where we develop and operate AI in-house, we will advance the development of frameworks and rules to ensure transparency, fairness, and safety, and to minimize security risks.
As security threats continue to intensify, we will continue to comprehensively, efficiently, and appropriately investigate and implement a variety of technical countermeasures.
Preparing for threats spreading around the world
Rebuilding our global network and bolstering our incident response structure
With the advance of globalization in modern society, companies are expanding their sites around the world and building international business networks. But with this comes expanded cyber security risks, at a global scale. Cyber attacks have become increasingly sophisticated and diverse, playing a part in conflicts or political disputes between nations, or as attacks for monetary gain by criminal organizations, and companies face an urgent need to take robust security measures in response. As the Mitsubishi Materials Group maintains Group companies and sites in 32 countries and regions around the world, it is necessary to not only prepare for these cyber attacks in Japan where our headquarters are located, but also across all our global operations.
Rebuilding our network
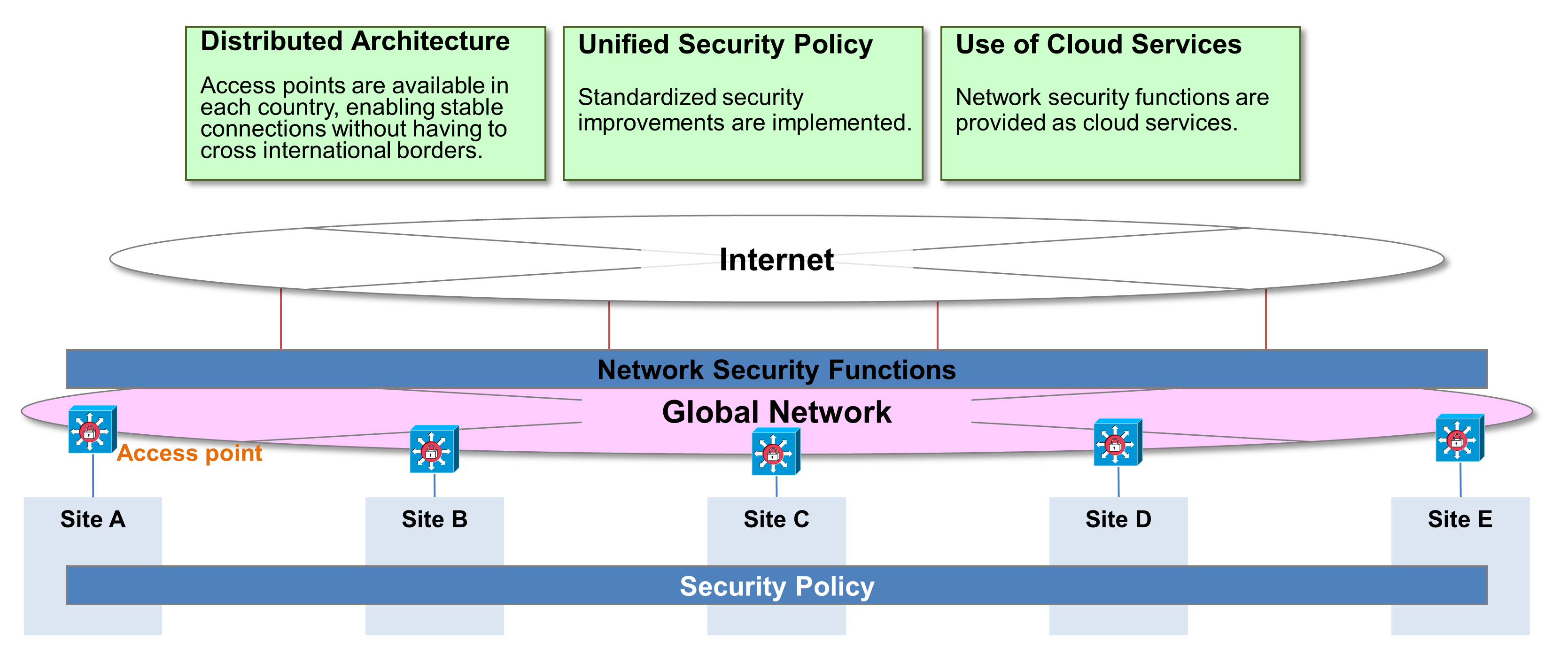
First of all, to counter the cyber threats faced by our companies, it is essential to rebuild our global network. In a conventional centralized network, an attack on central servers and data centers poses the risk of rendering the entire system dysfunctional. Preventing this requires the introduction of a distributed architecture. With a distributed architecture, each site is operated independently so that if one site is attacked other sites are not impacted. This improves the overall strength of security and distributes risks.
Standardization of security measures
Next, it is important to standardize security measures at a global scale. When each site employs individual security measures, those sites that fall behind in implementing measures become vulnerable and face a greater risk of being targeted by attackers. That is why it is necessary to formulate security policies that are unified across the Group and implement them consistently at each site. This makes it possible to maintain a uniform level of security overall and eliminate vulnerabilities at individual sites.
Additionally, network security functions can be provided as cloud services to apply consistent security policies even in distributed environments. This enables centralized security management for each site and remote worker, eliminates variability in security measures and maintains unified standards. Moreover, real-time threat intelligence can be utilized to provide the flexibility of being able to swiftly respond to the latest cyber threats.
Bolstering our incident response structure
Strengthening the incident response structure is another important part of security measures. We formulate incident response plans and clarify concrete response procedures to be followed in the event of a cyber incident. We also build information security systems that are operated globally and coordinate with administrators in each region to share information and develop unified response measures. By running drills and simulations on a regular basis, we boost employee response capabilities and verify the effectiveness of our plans. This enables us to respond in swift and accurate ways when an incident occurs to keep any damage to a minimum.
From Protection to Detection and Response
What are SOCs and CSIRTs?
With information security growing in importance year after year, approaches to safeguard the data and systems maintained by organizations are also evolving. To date, security measures emphasizing protection were the mainstay approach. But today, as the methods employed in cyber attacks become increasingly crafty and sophisticated, a defensive posture alone is insufficient. That is why there has been a focus on strengthening Security Operations Centers (SOCs) and Computer Security Incident Response Teams (CSIRTs).
An SOC is a dedicated team that monitors security for an organization's networks and systems and detects abnormal behavior in real-time. A CSIRT, meanwhile, is a team dedicated to responding in the event of a security incident. By having these teams coordinate, it is possible to respond to cyber attacks swiftly and effectively.
Shifting from Protection to detection
Conventional security measures have focused on protection with the use of firewalls and antivirus software. While these are important elements in preventing attacks from the outside, but due to diversifying attack methods, it has become increasingly difficult to maintain complete security through protection alone. For example, there are risks that breach defensive boundaries such as cases where an internal employee unwittingly downloads malware, or attacks launched through phishing emails.
This is what makes the role of an SOC crucial. By monitoring network traffic, analyzing logs and detecting suspicious activity, security incidents are discovered in real-time. Specifically, techniques include the detection of abnormal communication patterns and behavioral analysis of unknown malware. These approaches make it possible to detect potential threats at an early stage and swiftly respond to them.
Improved response
Not only detection but the response after an incident has occurred is of vital importance. The CSIRT formulates incident response plans and responds swiftly once an incident has occurred. Specifically, the team identifies the extent of damage, takes actions to keep the effects to a minimum, and undertakes restoration work. It is also important to uncover the methods and vectors of attack and take preventative measures through a forensic investigation conducted after the incident.
Strengthening coordination between the SOC and CSIRT
Improved coordination between the SOC and CSIRT results in a more effective security framework. If a workflow where the SOC rapidly informs the CSIRT of a detected anomaly and the CSIRT immediately initiatives a response can be established, damages can be kept to a minimum. Moreover, by having both entities regularly share information and engage in joint training, security awareness and response capabilities are enhanced throughout the organization. MMC has completed expanding SOC monitoring targets to PCs, on-premises servers, and cloud environments, and we aim to extend this coverage to control systems in the future.
Protecting manufacturing technologies
Strengthening OT security
Information technology (IT) generally refers to systems that save, process and communicate information, serving as the technology that supports business processes. Meanwhile operational technology (OT) represents the systems that control and monitor production equipment and devices, serving as the technology that directly supports the operation of plants and factories. Because of these differences, OT systems require real-time performance and high availability, and generally once they are installed, they are used for long periods and are difficult to modify. In recent years OT environments have also become digitized and seen the advance of IoT technologies, exposing them to an increased risk as the targets of cyber attacks. Once an OT system is attacked, it can lead to production line stoppages, reduced product quality, and depending on the severity, cause serious accidents that imperil people's lives. That is why strengthening OT security is a challenge of the highest priority for the manufacturing industry.
Challenges with OT security
Security challenges in OT environments are wide-ranging. First, since OT systems are designed to operate for extended periods, they often use older technologies and software, which can lead to vulnerabilities. In addition, since many OT systems operate on closed networks that are generally not connected to the Internet, their defenses against outside attacks can be inadequate.
And as IT and OT become increasingly integrated, there are growing risks of attacks on OT systems via IT systems. For example, there are examples of malware infections that have entered via IT systems spreading to OT systems, along with a growing risk of unauthorized operation utilizing remote access. To face off against these challenges, security measures designed to combine IT and OT are needed.
Specific measures to boost security
Measures to beef up OT security include the following. We adopted OT security guidelines in the fiscal year ended March 2024 and plan to steadily phase in measures going forward.
- Network segmentation: Clearly separating OT and IT networks and blocking unnecessary communications between them prevents the spread of attacks.
- Access control: We strictly manage access privileges to OT systems and implement access control based on the principle of granting the minimum required permissions.
- Patch management: We regularly update the software and firmware of our OT systems to patch known vulnerabilities. However, careful planning is needed to ensure stable system operation when applying patches.
- Monitoring and detection: We have strengthened OT network monitoring and have systems in place to detect abnormal activities and suspicious behavior in real-time.
- Incident response plans: We have clearly laid out the procedures to follow when responding to a cyber incident and conduct regular drills.